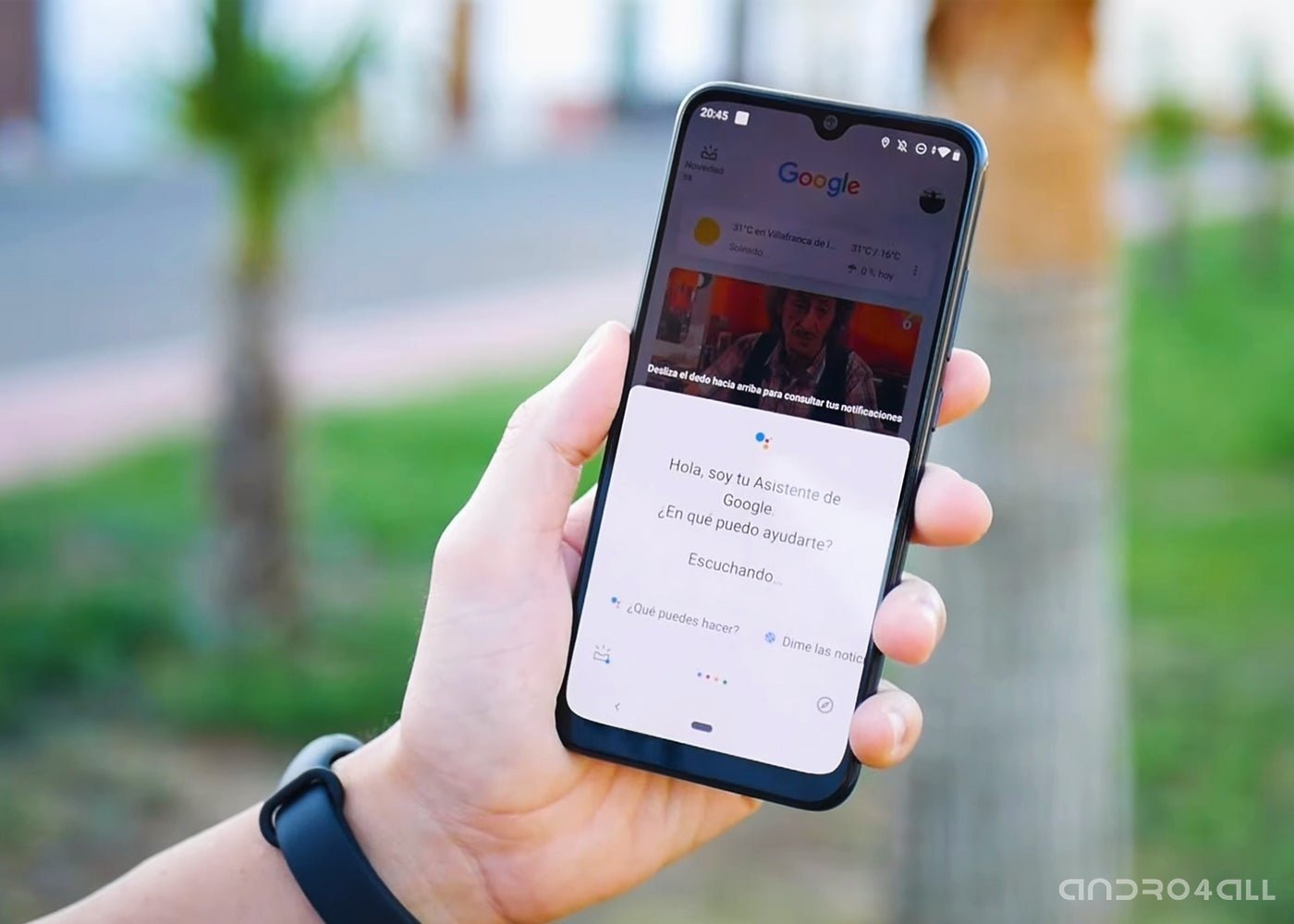
A group of researchers from the University of Washington at St. Louis calves a attack method of using mobile devices through affiliate assistants such as Siri or Google Assistant. Attacks are supported Vibration and Ultra that the assistant in question translates as voice commands, even though they may not be fully appreciated by the people.
In this way, the researchers were able to Do things like take pictures, get key or two-factor verification codes in text messages or adjust different device parameters such as volume level.
To achieve this, as described in the report, devices should be positioned more like a table wood, metal or glass, for the goods to allow Ultrasonic wave transmission In use.
They are hosted on an Android phone using Ultra and a table
Before panicking, it is important to emphasize that Investigators were able to perform these types of attacks
Either way, it is still amazing to know how it was possible to "trick" both Siri and Google Assistant to respond to instructions sent by ultrasound. To accomplish this, the researchers placed a microphone and piezoelectric sensation under the table. The first is used to listen to the auxiliary response, and the second to emit ultrasonic waves. In addition, a wave generator was used to convert signals for translation.
SurfingAttack allows new attack scenarios, such as the capture of a Short Message Service (SMS) mobile access code, makes fake calls without the owner's knowledge, etc. "
All of this, added to the software "SurfingAttack", has been approved by the investigating team successfully attacks a total of 15 devices variants, including Google Pixel 1, 2 and 3 or Galaxy S7 and S9. Also included are some of Apple's latest versions of Apple. However, it is very possible that most of the current smartphones can be attacked using these types of techniques. However, they explain that certain models are also curved back
This is not the first time it has been reported "remote" attacks targeting smart devices fitted with smart assistants. Recently, another group of researchers was able to “break” smart speakers using laser beams. However, in the same way as this new approach, it is unlikely that such attacks will be conducted regularly.
The investigators have enabled a website where they found more information about the project, as well as a glance functionality of "SurfAttack" in the "real world". Also included is a list of devices were able to attack successfully, and possible actions that could exploit this "danger".
Follow ANDRO4ALL
About Christian Collado
Growth Editor at Andro4all, specializing in SEO. I am studying software development and writing about technology, especially about the Android world and everything related to Google since 2016. You can follow me On Twitter, email me if you have something to tell me, or contact me via my LinkedIn profile.
My work group: