Today we store a huge amount of information on our iPhones. From health data to the messages we send to others, to all of our photos. In this context, it is more important than ever that we have the security and peace of mind that our data continues to be ours.
we already know that iPhones can’t have viruses and that it is extremely very difficult for someone outside to have compromised them, but there are other ways for someone to spy on us from our iPhone. Fortunately, it can be easily detected and quickly remedied.
A very unusual and easy to solve situation
As we just said, with the exception of ultra-targeted attacks like Pegasus, iPhones are practically invulnerable to threats of this type
Luckily for us, since we would have installed an app and certificate ourselves, recovering control of the iPhone is as easy as removing them. Let’s look at both cases in detail. A malicious application may ask us to access more data than is needed to transmit it to a third party. To detect and fix it, follow these steps:
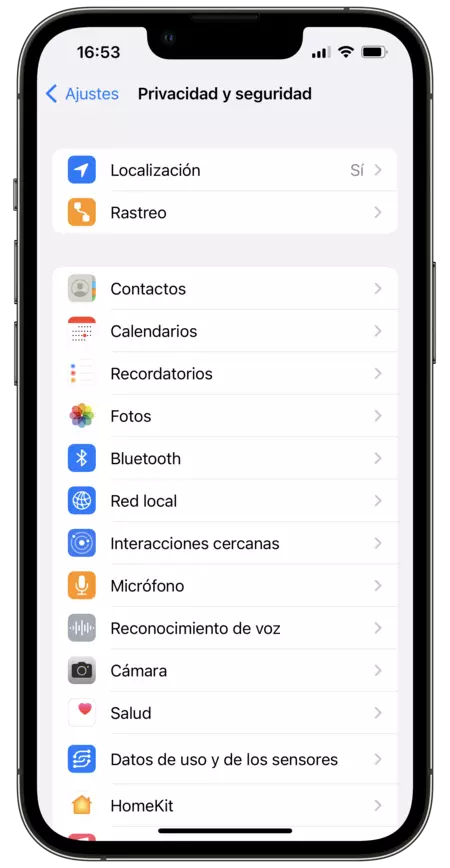
- We open the application The settings on our iPhone or iPad.
- We entered Privacy and Security.
- We entered contacts, calendars, Camera Pictures, etc. and we look at which apps have access.
- Those that don’t just need to be disabled to prevent them from continuing to access our data.
If we detect an application that we think is suspicious, we search Spotlight for its name and, once found, we keep it for to select
The second hypothesis, that of the profiles, is clearly much more dangerous. For example, a profile can force all iPhone traffic to go through a compromised VPN, potentially exposing our passwords. You can also change the settings of certain aspects of the phone to make it easier to expose data. In other words: never, ever, ever install a configuration profile which we do not trust very clearly and which we can verify.
Like before, an oversight on our part in this respect is easy to correct, because we can uninstall any profile just by following a few steps. Which? These:
- We open the application The settings on our iPhone or iPad.
- We entered General.
- we play in VPN and device management.
- Under “Configuration Profiles” we’ve gone through the list.
- Anyone we see suspicious, we touch then choose Delete profile.
If necessary, we restart our iPhone or iPad. The recommendation here is that, if we don’t know why a profile is installed, we remove it immediately. The use of these profiles is very rare, although in the business world it may be more common, if in doubt it is probably best to be on the safe side.
Covered these two fronts, the odds of an iPhone being compromised are exceptionally low. In any case, and as we have just seen, it is our responsibility not to accept applications, e-mails, messages, links and other types of similar material from untrusted sources. When in doubt, let’s think it through and ask that the security of our data is in our hands.
In Applesphere | How and Why to Disable Access to Notification Center When iPhone is Locked









